Building a Threat Response API with FastAPI: A Comprehensive Guide
Written on
Chapter 1: Introduction to Threat Response APIs
In the realm of cybersecurity, there are numerous APIs available for threat intelligence, with AbuseIP being a notable mention due to its no-cost access. While utilizing this API directly is an option, I will demonstrate how to build my own version that integrates theirs. This approach allows for the incorporation of multiple APIs, enriching the collected data.
To begin, the first step is securing a hosting solution. Personally, I prefer cloud hosting services, with IONOS being my go-to due to its affordability. Alternatively, platforms like Azure and AWS offer free tiers that can be advantageous.
On my IONOS account, my "Dev" hosts are priced around £2.40 per month.

Chapter 2: Setting Up Your Hosting Environment
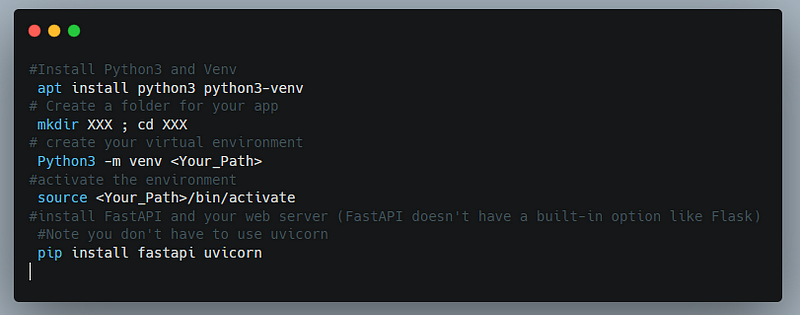
For this project, I will utilize a low-spec Debian server. Once connected, the next step is to install the necessary components.
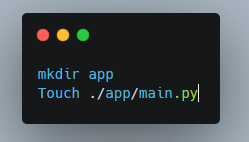
After completing the installation, create a directory for your application and establish a Python file named main.py.
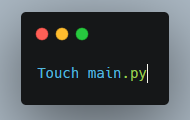
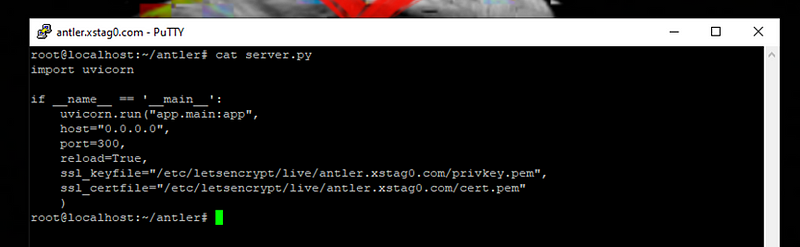
Then, create a server.py file which will reside in the main directory.
Optional:
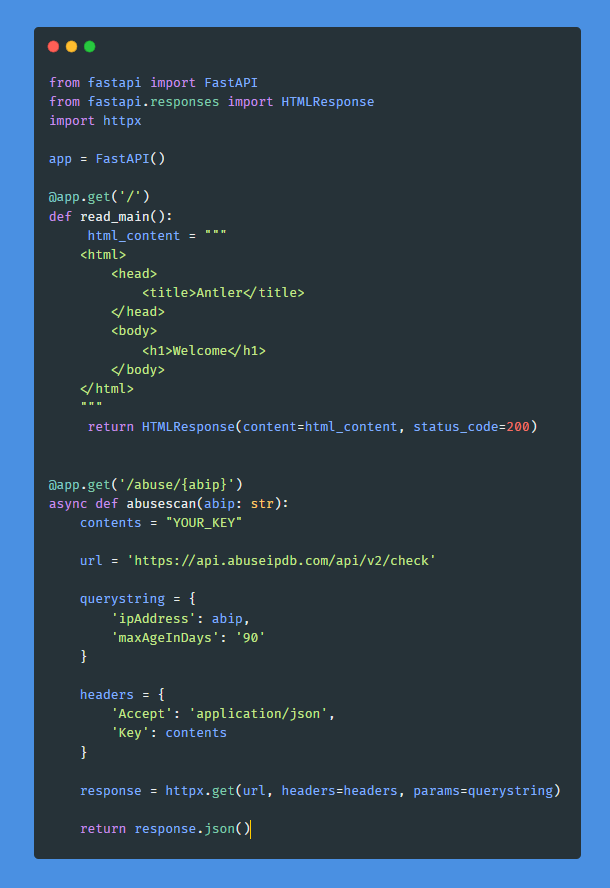
With the foundational setup complete, it’s time to delve into the coding aspect. Edit your main.py file and input the necessary code. For reference, you can find the code on GitHub.
Chapter 3: Understanding the Code Structure
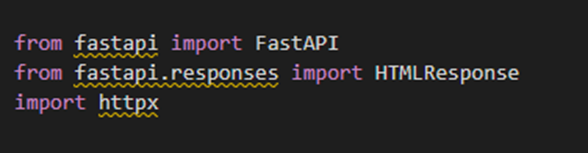
Let’s break down the code to clarify its components. Initially, we import the libraries required for our application.
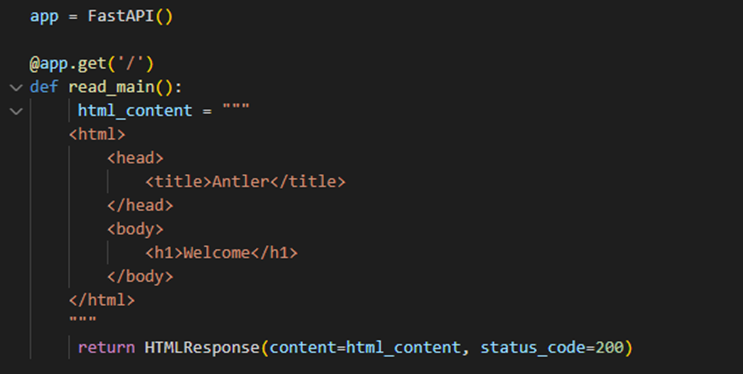
Next, we define the app and set up a simple HTML page to display on the default path.
While this setup is not mandatory, it serves as a useful example:
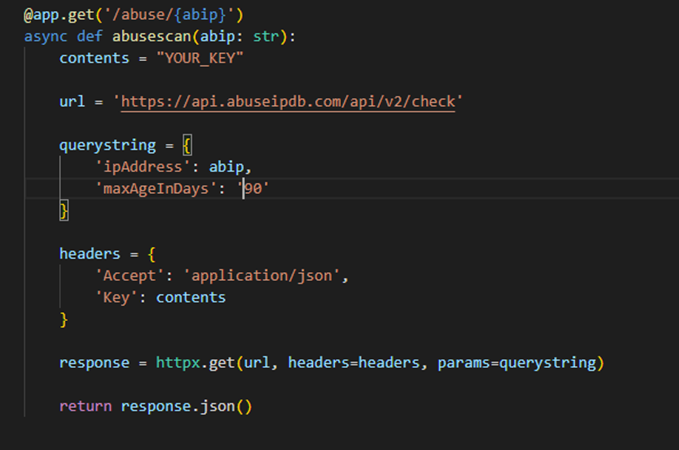
In this example, I've opted to use httpx, but there are various alternatives available. If you're following along, be sure to update the contents with your API key, which can be found on your AbuseIP account.
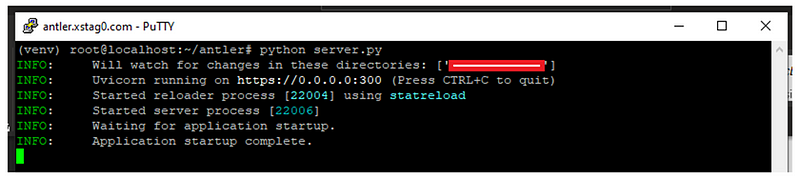
Once your main.py file is prepared, you can run the application using the following command:
To verify that everything is functioning correctly, open your browser and access the relevant URL.
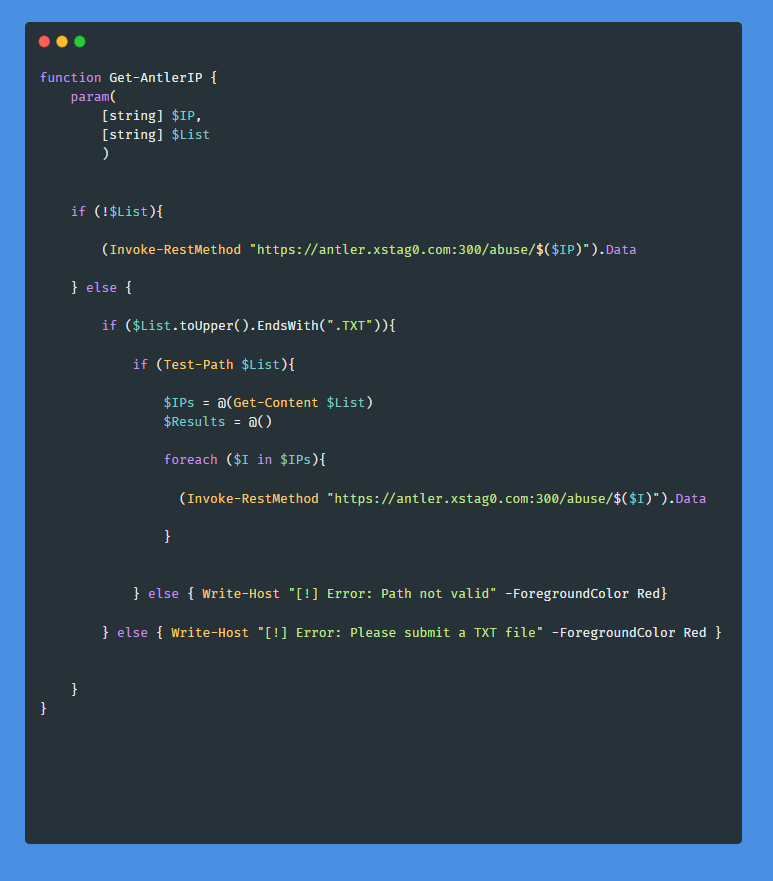
Now you have a basic API that you can expand upon. For instance, you could create a PowerShell function to enable users to query one or multiple IPs without needing a central script or an API key.
To query a single IP:
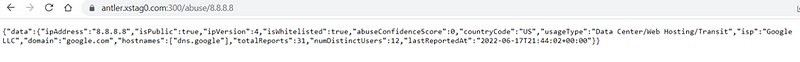
To query multiple IPs:
Additionally, you can utilize this API to enhance data within your security platforms. If your Extended Detection and Response (XDR) or Endpoint Detection and Response (EDR) systems support "Web Hooks," your API can automate parts of your incident response by returning the necessary data.
Keep in mind that some solutions may send a full JSON request, so parsing and filtering on the API side will be essential. This effort can yield long-term benefits.
Before concluding, here are some recommendations:
- Avoid running your application as root.
- Restrict inbound requests through your firewall if feasible.
- Never store API keys directly in production code.
- Enjoy the process!
The final takeaway is to embrace creativity and exploration. With FastAPI or Flask, you have the opportunity to combine various solutions into something remarkable.
Chapter 4: FastAPI Tutorials
For further learning, check out these helpful video tutorials:
The first video, "Python FastAPI Tutorial: Build a REST API in 15 Minutes," provides a quick overview of constructing a REST API using FastAPI.
The second video, "API Integration Course – Modern Python with FastAPI," dives deeper into API integration with modern Python practices.